WHAT IS CRYPTOGRAPHY?
What is Cryptography?
In this article, I shall discuss What is cryptography? And other things that has to do with cryptography, like cypherpunk, cryptographer, cyptanalysis and quantum cryptography.
What Is Cryptography?
Cryptography is the art and science of making a cryptosystem that is capable of providing information security.

Cryptography deals with the actual securing of digital data. It refers to the design of mechanisms based on mathematical algorithms that provide fundamental information security services.
You can think of cryptography as the establishment of a large toolkit containing different techniques in security applications.
Cryptography is a method of protecting information and communications through the use of codes, so that only those for whom the information is intended can read and process it. The prefix “crypt-” means “hidden” or “vault” — and the suffix “-graphy” stands for “writing.”
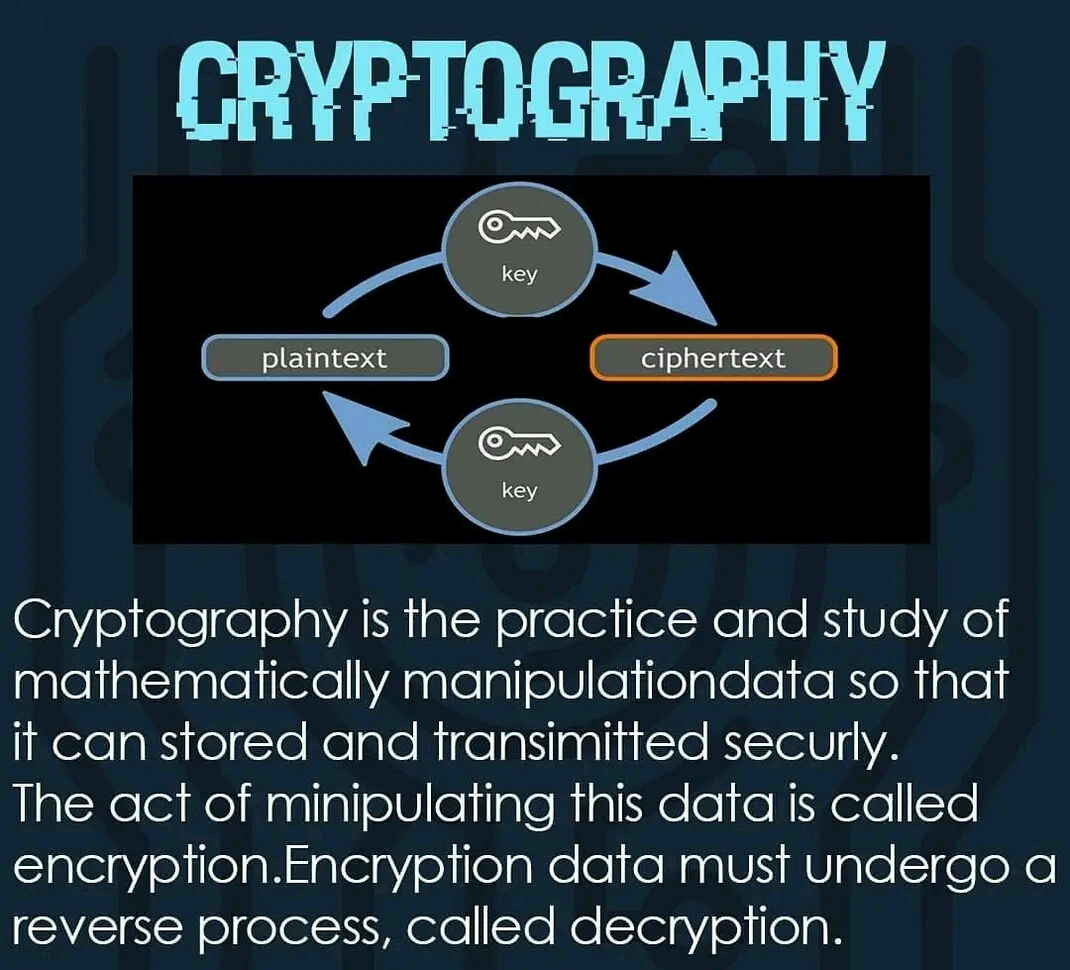
In computer science, cryptography refers to secure information and communication techniques derived from mathematical concepts and a set of rule-based calculations called algorithms, to transform messages in ways that are hard to decipher. These deterministic algorithms are used for cryptographic key generation, digital signing, verification to protect data privacy, web browsing on the internet, and confidential communications such as credit card transactions and email.
Modern cryptography concerns itself with the following four objectives:
Confidentiality: the information cannot be understood by anyone for whom it was unintended
Integrity: the information cannot be altered in storage or transit between sender and intended receiver without the alteration being detected
Non-repudiation: the creator/sender of the information cannot deny at a later stage his or her intentions in the creation or transmission of the information
Authentication: the sender and receiver can confirm each other’s identity and the origin/destination of the information.

Cypherpunk
The use of cryptography was primarily restricted to military forces and intelligence agencies until the 1970s.
What you see in the image below is a tool used in military cryptography.

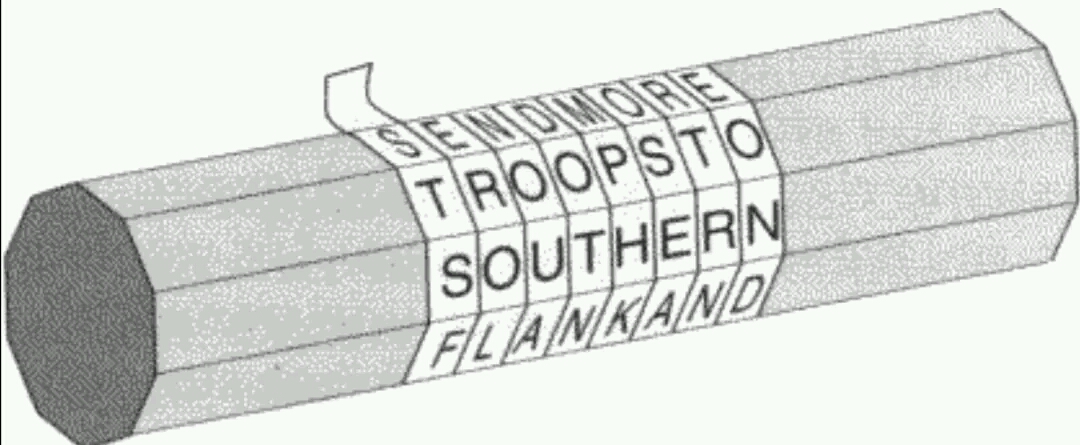
It’s the SCYTALE : a wooden stick around which a strip of leather or parchment containing the coded messages was rolled up. It was used in Sparta in the 5th century B. C. To decipher the message the recipient had to wrap the strip on a scytale of the same diameter as that of the sender.
U.S National Bureau of Standards and the National Security Agency developed this technology. New Directions in Cryptography was published in 1976 by pioneering cryptographers Whitfield Diffie and Martin Hellman. The mailing lists discussed a wide range of topics, including mathematics, cryptography, computer science, and politics.
About a decade before they became a public issue, cypherpunks challenged government surveillance and corporate control of information. In addition to Pretty Good Privacy (PGP), they also developed a number of cryptography-based privacy applications. The concept of Bitcoin was developed using the ideas and accomplishments of cypherpunks. Among the members of the Cypherpunks are well-known crypto experts Nick Szabo and Adam Back.
The cypherpunk movement advocates the use of powerful cryptography and technology to protect the privacy of individuals.
Cypherpunk has been in use since the 1980s. Science fiction, dystopian, and futuristic elements are common elements of the fiction genre. As computing demonstrated its potential for securing public information using cryptography in 1970, the cypherpunk movement was born. An individual who utilizes cryptography as a means of communication is referred to as a cypherpunk.
A significant contribution made by cypherpunk to the development of the Internet, secure remote access, and the advancement of computer technology and cryptography has been the development of the Internet. A significant amount of progress has been made in cryptography as a result of cypherpunks.
Cryptographer
Surveillance expert
A cryptographer is an expert in secrets, he knows how to find secrets and how to keep secrets. A savvy hacker and cryptographer, he uses aerial drones to covertly spy on opponents in Apex competitions. It was discovered that his drone design has many similarities with the drone of the wanted murderer Park Tae-joon.
Orphaned on the streets of Sotamo, Tae-joon and his foster sister, Mira Alexander, escaped a life of poverty by becoming computer engineers, designing drones that broadcast Apex races across the frontier. But one day, Tae-joon disappears along with important company secrets, and his sister disappears under mysterious and violent circumstances. However, the cryptographer claims that he has nothing to do with Tae-joon, and the case remains unsolved to this day.
Cryptographer’s motivations for joining the Apex competition are as mysterious as he is. In recent interviews, he proclaimed that he was seeking justice… but no one knew exactly.
Tactical Skill: Surveillance Drones
Deploy an aerial drone to give you a bird’s-eye view of your surroundings. When a drone is destroyed, it must wait for a forty second cooldown before deploying another.
Passive Skill: Neural Link
Marks enemies detected by surveillance drones within 30 meters of your position, making them visible to you and your teammates.
Trick: Drone EMP
Your Surveillance Drone unleashes an EMP that deals shield damage, slows enemies, and destroys traps.
What is Cryptanalysis?
The art and science of breaking the cipher text is known as cryptanalysis.

Quantum Cryptography is the future of hacking. It’s the only way to make hacking futile—and it’s so much fun!
What if we tell you that making hacking efforts futile is as easy as using quantum cryptography?
That’s what Maverick Globals has done, and they’re just getting started.
Quantum encryption allows users to send information securely while making it impossible for anyone else to read it. In fact, the only thing that can read it is the person who sent it!
And now Maverick Globals wants to take this technology even further. They’ve developed a way to use quantum cryptography so that hackers can’t even know what kind of data they’re trying to steal—they’ll simply disappear.
SEE ALSO : WHAT ARE CRYPTOCURRENCY MINING AND STAKING AND HOW DO THEY WORK?
Hacking is a different level, to escape from being a victim, here is a pro tip for you:
The first thing we’ll do is give you our best tips for avoiding hackers: don’t click on links in spam emails unless you know exactly what they’re about, never download software from suspicious sites, and always follow security updates that are sent out by your operating system provider.
Comments are closed.