HOW TO PREVENT SQL INJECTION

HOW TO PREVENT SQL INJECTION
Let’s start with What is SQL Injection attack and its types before discussing its prevention.
What is SQL Injection?
SQL stands for Structured Query Language.
Any website that is database driven and that is the majority of websites is susceptible to SQL injection attacks.
An SQL query is a request for some action to be performed on a database, and a carefully constructed malicious request can create, modify or delete the data stored in the database, as well as read and extract data such as intellectual property, personal information of customers, administrative credentials or private business details.

SQL injection is a type of web application vulnerability that allows an attacker to inject malicious SQL statements into an application’s input fields. The vulnerability arises when an application fails to properly validate and sanitize user input before using it in an SQL query.
An attacker can exploit this vulnerability to gain unauthorized access to sensitive data, modify or delete data in the database, execute arbitrary SQL commands, and even take control of the entire application or the underlying server.
For example, consider an application that allows users to search for products by entering a product name. If the application fails to properly validate and sanitize the user input, an attacker can enter a malicious SQL statement as the product name, such as “‘; DROP TABLE products; –“. This SQL statement will be executed by the application, which can result in the deletion of the entire “products” table.
Types of SQL Injection
SQL injection attacks can be classified into two types:
1. In-band SQL injection
In-band SQL injection attacks are the most common type, where the attacker is able to retrieve the results of the injected SQL statement using the same channel as the vulnerable application.
2. Out-of-band SQL Injection.
Out-of-band SQL injection attacks, on the other hand, use a separate channel to retrieve the results of the injected SQL statement, such as an email message or a DNS query.
SQL injection attacks can also be further categorized into different types based on the attack vectors and techniques used by the attacker.
Some common types of SQL injection attacks include error-based SQL injection, union-based SQL injection, boolean-based SQL injection, time-based SQL injection, and blind SQL injection.
In an error-based SQL injection attack, the attacker exploits an SQL error generated by the application to infer information about the structure and content of the database.
In a union-based SQL injection attack, the attacker uses the UNION SQL operator to combine the results of two or more SQL queries and retrieve data from different tables.
In a boolean-based SQL injection attack, the attacker uses Boolean logic to infer information about the database.
In a time-based SQL injection attack, the attacker uses delay statements to infer information about the database.
And in a blind SQL injection attack, the attacker is unable to retrieve the results of the injected SQL statement and must rely on other techniques to infer information about the database.
SQL injection attacks are a serious threat to web applications, as they can lead to data breaches, loss of confidential information, and even system-wide compromise. According to the OWASP Top 10, SQL injection is one of the most common and dangerous vulnerabilities in web applications.
One of the main reasons why SQL injection attacks are so common is because many developers do not fully understand the risks and the techniques used by attackers. They may also be under pressure to deliver applications quickly and may not have sufficient resources to properly test and secure their code.
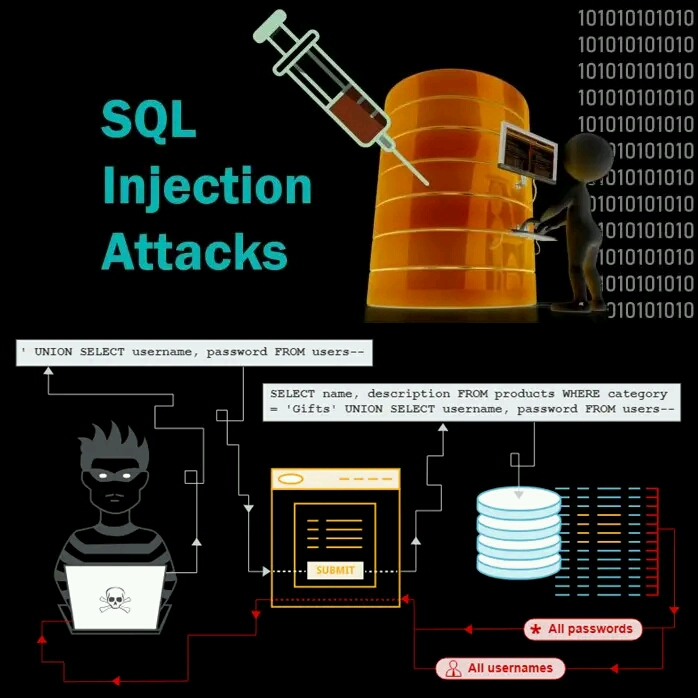
How to Prevent SQL Injection
This can allow the attacker to gain access to sensitive data, modify data or even execute arbitrary commands on the database server.
To prevent SQL injection, consider the following best practices:
Use parameterized queries: Parameterized queries use placeholders for input values, which are then passed separately as parameters to the database. This prevents attackers from injecting malicious SQL code into the query.
Use prepared statements: Prepared statements are similar to parameterized queries, but the query is prepared once and then executed multiple times with different input values. This can be more efficient than parameterized queries, especially for complex queries.
Validate user input: Input validation can help prevent attackers from entering malicious SQL code. Validate user input on both the client and server sides, and use whitelisting to only allow certain characters and values.
Use least privilege: Give users the minimum amount of privileges necessary to perform their tasks. This can limit the damage that an attacker can do if they are able to inject malicious SQL code.
Use stored procedures: Stored procedures can be used to encapsulate database logic and can help prevent SQL injection by limiting the types of queries that can be executed.
Keep software up to date: Keep your database and application software up to date with the latest security patches to ensure that known vulnerabilities are addressed.
Escape special characters: If you cannot use parameterized queries or prepared statements, escape special characters in user input. This involves adding a backslash before characters that have special meaning in SQL, such as quotes and semicolons.
Use a web application firewall: A web application firewall can detect and block SQL injection attacks by analyzing incoming requests and responses.
Avoid dynamic SQL: Dynamic SQL involves constructing SQL statements on the fly using user input. This can be vulnerable to SQL injection attacks, so it’s best to avoid it if possible.
Limit error messages: Limit the amount of information that error messages reveal, as attackers can use this information to craft SQL injection attacks. Instead, provide generic error messages that do not reveal sensitive information.

Log and monitor SQL activity: Log and monitor all SQL activity to detect and respond to suspicious behavior. This can help identify SQL injection attacks and other types of malicious activity.
Train developers and users: Train developers and users on best practices for preventing SQL injection attacks. This can include explaining the risks of SQL injection, providing code examples for secure database access, and teaching users how to enter input values that are safe for SQL queries.
Use a secure connection: Use secure connection methods such as SSL/TLS to encrypt data transmitted between the database server and the application server. This can prevent attackers from intercepting and modifying data in transit, including SQL statements.
Limit exposure of the database: Limit access to the database server and its associated resources to authorized personnel and systems only. Avoid exposing the database to the internet or other untrusted networks, and restrict access to the database from the application server to only necessary IP addresses.
Use security-focused programming practices: Use security-focused programming practices such as code reviews, threat modeling, and testing to identify and address security vulnerabilities in your application code. Avoid using dynamic SQL whenever possible, and use parameterized queries or prepared statements instead.
Monitor database activity: Monitor database activity logs for unusual or suspicious behavior, such as repeated failed login attempts, unusual query patterns, and unexpected changes to the database schema. This can help detect SQL injection attacks early and limit their impact.

Regularly test for vulnerabilities: Regularly test your application and database for vulnerabilities using tools such as vulnerability scanners and penetration testing. This can help identify and address security issues before they are exploited by attackers.
Use database auditing: Database auditing can help track changes to the database schema and data, as well as identify security-related events such as failed logins and suspicious query activity. This can help detect SQL injection attacks and other security incidents.
Use encryption: Use encryption to protect sensitive data stored in the database, such as user credentials and personal information. This can help prevent attackers from accessing and reading the data even if they manage to inject malicious SQL code.
Use a database firewall: A database firewall can analyze incoming database traffic and block unauthorized queries, including SQL injection attacks.
Use input validation libraries: Use input validation libraries such as OWASP ESAPI or PHP’s filter_input function to validate user input and prevent malicious SQL injection attacks.
Follow secure coding practices: Follow secure coding practices such as input validation, output encoding, and error handling to reduce the risk of SQL injection attacks. Use libraries and frameworks that provide built-in security features, such as input validation and prepared statements.
Use multi-factor authentication: Use multi-factor authentication to add an extra layer of security to user authentication. This can help prevent attackers from accessing the database even if they manage to obtain valid user credentials through a SQL injection attack.
Conduct regular security training: Regularly conduct security training for all personnel who interact with the database, including developers, administrators, and users. This can help raise awareness of security risks and ensure that everyone is following best practices for preventing SQL injection attacks.
By implementing these additional tips, you can further reduce the risk of SQL injection attacks and improve the overall security of your database and application.
SEE ALSO : 38 PROFITABLE TECH BUSINESSES YOU CAN DO IN 2023
In addition to these measures, organizations can also leverage security tools and services to help detect and prevent SQL injection attacks. For example, web application firewalls (WAFs) can provide an additional layer of protection by blocking requests that contain suspicious SQL statements or patterns. Security testing and vulnerability scanning tools can also help identify potential vulnerabilities in web applications and databases.
SEE ALSO : SOCIAL MEDIA PLATFORMS THAT PAY USERS FOR CREATING AND SHARING CONTENTS IN 2023
Challenge in Preventing SQL Injection Attacks
One of the biggest challenges in preventing SQL injection attacks is the sheer number of potential entry points for an attacker to exploit. It is common for web applications to have numerous user input fields, including text boxes, drop-down menus, and checkboxes, all of which can be manipulated to execute SQL queries.
SEE ALSO : HOW YOU CAN RUN IOS APPS ON YOUR ANDROID PHONE DEVICE
Another challenge is that SQL injection attacks can be difficult to detect, especially if the attacker uses techniques to obfuscate their malicious code. For example, they may use encoded or encrypted input or split the malicious SQL code across multiple input fields.
SEE ALSO : Advantages And Disadvantages of Blogging And Vlogging
The injected SQL code can often blend in with legitimate SQL statements. This can make it difficult for security teams to identify and mitigate the attack before it causes damage.
Comments are closed.