Six Phases of A Penetration Test And The Aspects of The Process That Are Essential for Success
Six Phases of A Penetration Test And The Aspects of The Process That Are Essential for Success
In this article, we are diving into the six phases of a penetration test and we shall learn about what aspects of the process are essential for success. Following this methodology is extremely useful to professional pentesters and amateur hackers alike.
Your organization should know the dangers out there. It should assess threats facing its applications, enabling the business to better protect its systems and data from malicious attacks. Vulnerabilities can be found in applications from third-party vendors and internally made software, but most of these flaws are easily fixed once found.
To do this, you must assess and test. There are many types of testing, these are collectively known as ‘Vulnerability Assessments and Penetration Testing’ (VA/PT). Classical ‘Penetration Testing’ means that tests are performed from the perspective of an attacker, and vulnerabilities are exploited to see ‘how far an attacker can get’.
However, this is not always the most effective way of testing because it often makes more sense to perform a Vulnerability Assessment: test in such a way that as many vulnerabilities as possible are found without wasting time trying to exploit them to see how far you can get. Finding more vulnerabilities is often more valuable because it allows to reduce risks more effectively: exploring wide, instead of (only) deep.
What is a Vulnerability Assessment, and what do I gain from it?
In short, a vulnerability assessment is a security procedure providing a detailed overview of your IT infrastructure where vulnerabilities get identified and classified in severity levels. A detailed remediation report will be provided outlining necessary and recommended mitigation steps.
This process provides you with a better understanding of your IT security risks and a guide to remediate issues and strengthen your IT security and application standards to greatly reduce the likelihood that a cybercriminal will be able to gain unauthorized access to your organisation.
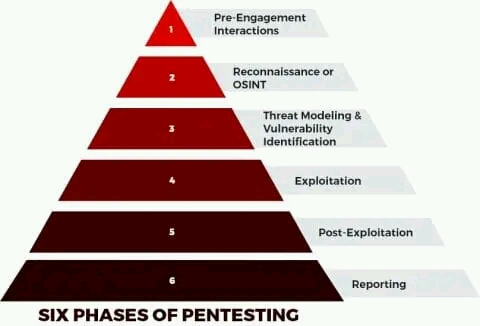
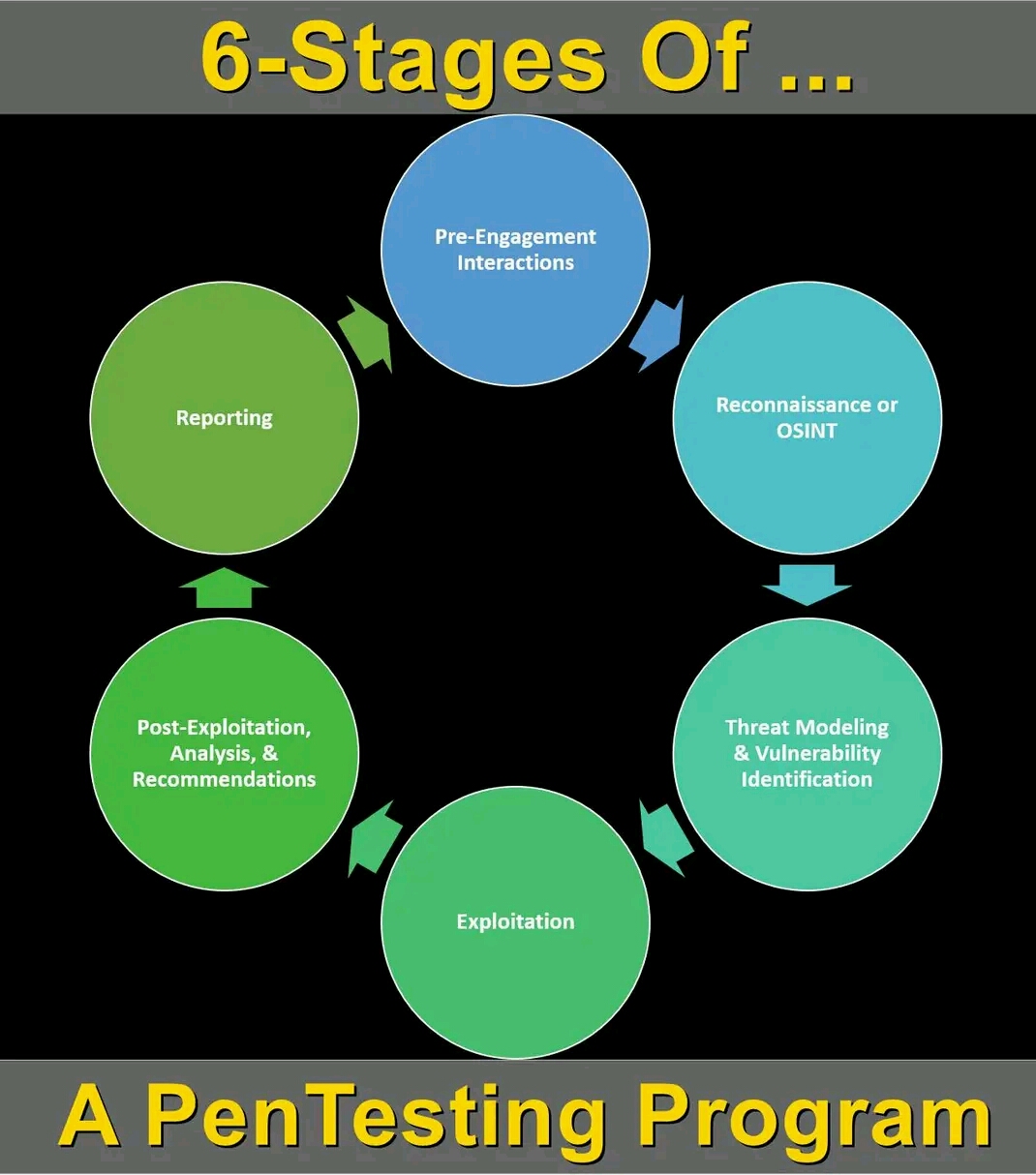
Six Phases of A Penetration Test
What Is Penetration Testing?
Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues.
In a professional penetration test, there are six phases you should know.
? Pentesting Lingo
Like many industries, and especially within IT, certain terms can cause initial confusion for people not familiar with them. Penetration testing can get pretty technical, but some of the confusion comes from words that are used before the engagement even begins.
A pentest can either be internal or external. An internal test means the pentester starts inside the network and usually has some sort of access as if they were simulating a rogue employee or an attacker who has breached the perimeter. An external test begins outside the network or system, which most closely resembles a real-world attack.
There are three additional categories to internal versus external testing which describe the level of access the pentester has:
• White box testing gives the most access, and the tester will often be given a list of hosts, IP addresses, source code, and even credentials.
• Black box testing, on the other hand, assumes the pentester knows very little about the system and basically starts blind. This type of testing simulates an attacker’s point of view and can be useful for discovering vulnerabilities on the perimeter of the network.
• Gray box testing is the third type, which lies somewhere between white and black box testing.
Phase 1: Pre-Engagement
The first step of a penetration test mostly involves planning and preparation. It’s essential to figure out precisely what the plan of attack is before any testing actually begins, even though things will likely change and evolve later on. Tools that will be used should be selected at this point, as well as any scripts and accessories that might be useful. The decision to what type of testing (black or white box, internal or external) is also made during this stage.
In addition to the technical details, it is essential to define the scope of the engagement and any legal implications that may arise. This means having a clear definition of what is available to attack and what isn’t. The worst thing that could happen during a pentest is bringing down a production system or dropping a database just because someone went out of scope. The tester will also want to get a contract in writing that will protect them from any legal recourse should things go wrong.
Now that the goals, expectations, and risks are clearly outlined for the client, the actual testing can begin.
Phase 2: Reconnaissance
The next phase of a penetration test is reconnaissance. This is where information gathering takes place — a vital step for the whole process. Insufficient quality data undermines the rest of the pentest because, without it, time gets wasted going down rabbit holes, and the real potential impact of any vulnerabilities is diminished.
Recon covers many different areas and can vary in terms of effort and activity. For instance, running a WHOIS query or gathering other DNS information is relatively passive. OSINT (open source intelligence) refers to any information that can be collected from public sources and can often yield significant results, especially with the prevalence of social media and other types of open communication used by organizations today.
More active forms of reconnaissance involve port scanning, network and service enumeration, banner grabbing, and packet sniffing. This is where all the juicy information is discovered and later used to determine if any vulnerabilities are present. Social engineering and physical recon methods will also sometimes be used, which range from phishing and impersonation to tailgating and dumpster diving.
Phase 3: Vulnerability Analysis
After sufficient information is collected, the pentester will need to determine what vulnerabilities are present and figure out the best path forward. Both automatic vulnerability scanners and manual testing can be utilized during this phase, although a combination of the two is often the optimal solution.
It is important to note the difference between vulnerability analysis during a penetration test and a vulnerability assessment. A vulnerability assessment is often its own separate thing — usually, an automatic scan takes place, and the results are reported to the organization, with no attempts at exploitation taking place.
There are two mains steps to the vulnerability phase. The first is merely identifying all possible vulnerabilities. Generally, the chance of successful exploitation is higher if more vulnerabilities are found. The second step involves reducing the number of vulns to those that have the highest probability of being valid and that require the least effort to exploit.
Phase 4: Exploitation
This part of the pentest is where the magic happens. The main goal of this phase is to gain access to the system and bypass the security controls in place. Exploitation makes up the bulk of the penetration test and can often take quite some time, which is a good thing for the organization being tested since this is the point where attackers would actually breach the system in the wild.
There are countless tools and frameworks out there designed to aid pentesters in the exploitation phase, both open and closed source. Some of these include Metasploit, Cobalt Strike, sqlmap, and Canvas. While these tools are useful and can save a lot of time, manual testing and human intuition are usually required.

Phase 5: Post-Exploitation
The post-exploitation phase is used to maintain control of the machine and to compromise the network and systems further. This is also where the value of the compromised device or system is determined, usually by the sensitivity of the data that is present or the usefulness in gaining a stronger foothold across the network.
In this stage of the pentest, it’s vital to gather as much information as possible that could be used against the organization or that could result in future exploitation. Things like credentials, password hashes, personal details, financial data, source code, or any other sensitive information should be obtained. Anything else that could be used to gain access to the system in the future is also a high-value target.
The last step of post-exploitation is cleanup. Any scripts, files, or backdoors that were used on the targets should be deleted, and any settings that were changed need to be reverted. If any new user accounts were created during the pentest, these need to be removed as well.
Phase 6: Reporting
The final step of a penetration test is reporting. While it isn’t the most exciting aspect of the process, it is arguably the most important. Results need to be clear and detailed for the organization to address any problems adequately. The report should clearly define the objectives, scope, methodology, and summary of the penetration test.
Reports will often be divided into different sections for the executive level as well as the security team. Highlights for executives will include a high-level overview of the engagement, potential business impact, a future roadmap, risk ratings, and a glossary of terms.
The technical part of the report is meant for the organization’s security team. It will include things like screenshots, proof-of-concept (PoC) code, details about the vulnerabilities discovered, steps to reproduce, various metrics, and possible remediation steps going forward.
Pentesting Is Useful for Both Pros & Amateurs
SEE ALSO : How And Ways to Step-up Your Game in The Python Programming Arena
Hope this article on Six Phases of A Penetration Test And The Aspects of The Process That Are Essential for Success is helpful?
Comments are closed.